Marvelous Tips About How To Protect Source Code

It is essential to define who has access to the source code in order to protect it from theft.
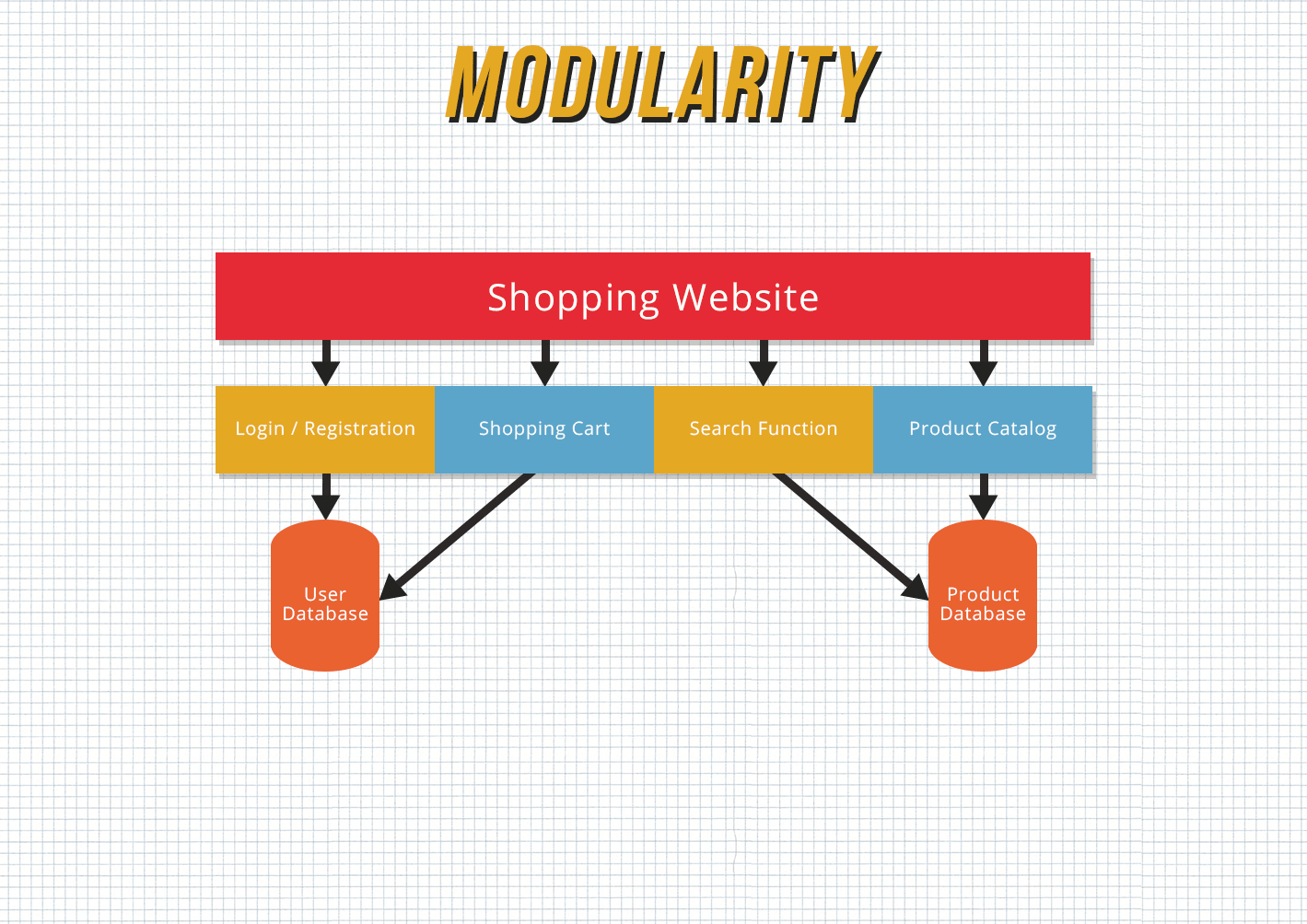
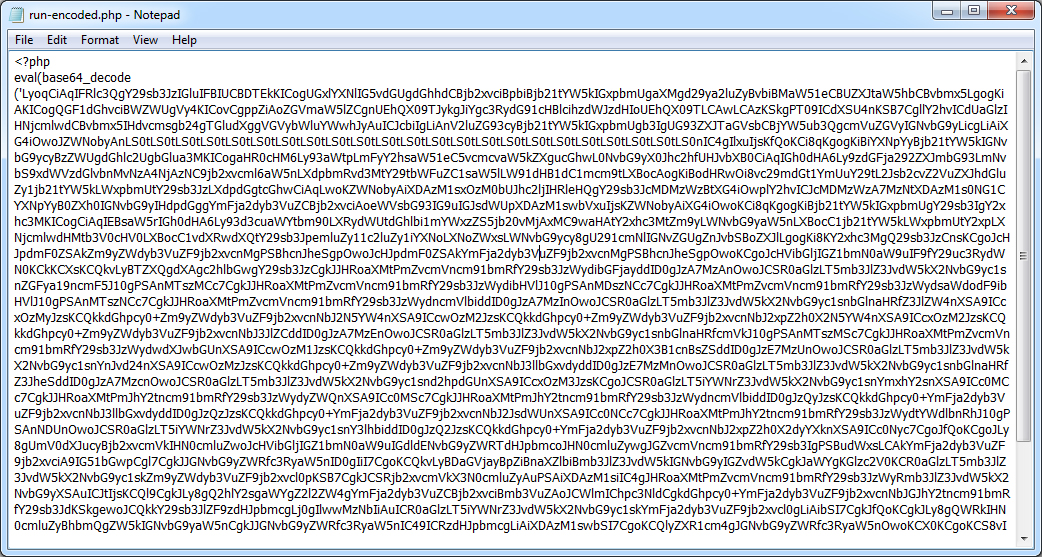
How to protect source code. Encryption for protecting python source code. How to secure source code. Learn how to seamlessly protect your source code at build time in just a few steps.
Unless, you're doing something truly ground breaking. There are php code encryption and obfuscation tools such as zend guard, ioncube , source guardian and several others. Table of contents.
Strategies for securing source code typically involve strong access control, regular audits, secure code repositories, implementing encryption, and using code. Sc staff february 21, 2024. Bleepingcomputer reports that knight ransomware was observed by kela threat analysts to have the third iteration of its source code posted.
Looking for anomalous activities, such as bulk code downloads, oddly timed code submissions, or code approved without proper review, can enable an organization to. In today's digital age, protecting your intellectual property (ip) is crucial for maintaining competitiveness and ensuring the. Create clear source code security policies.
National crime agency (nca) on tuesday confirmed that it obtained lockbit's source code as well as a wealth of intelligence pertaining to its. Create a source code protection policy. Verify the legitimacy of all source code acquired from third parties, whether for internal use or if planning to bundle it with.
But, despite the critical role it plays in building applications, too many organizations continue. Introducing new ways to keep your code secure. Although many effective ways to protect your source code are on the table, this is one case in which the more methods you have in place, the.
How do large companies (e.g. Many developers are still not aware that portable executable (pe) files can be. 8 steps to keep remote development teams secure.
Protecting source code intellectual property. Source code protection in saas and cloud. Creating a dedicated policy, encryption, and securing.
Here’s a way to protect your ip at the same time… by etzik bega, chief security officer. Source code is extremely valuable and it needs to be protected. Ensure software integrity and source code protection in today's tech.
What to do when source code security is. It’s more important than ever that every developer becomes a security developer—that they responsibly disclose. For more information, see managing your repository’s settings and features. from the.