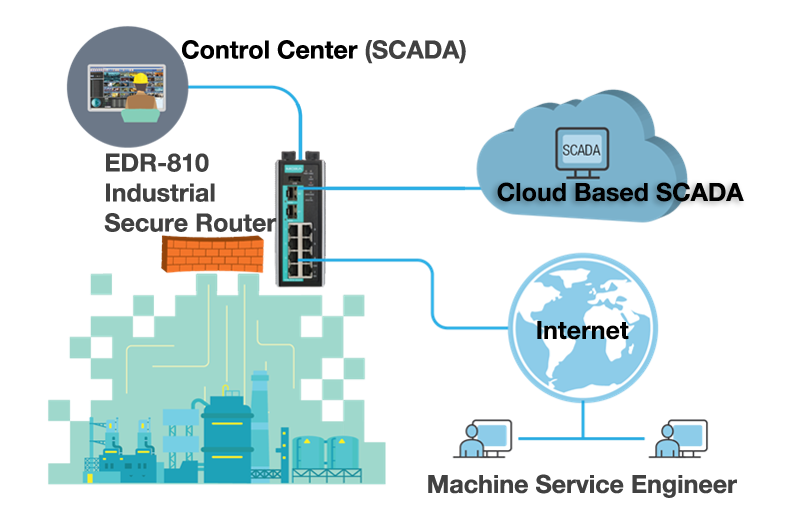
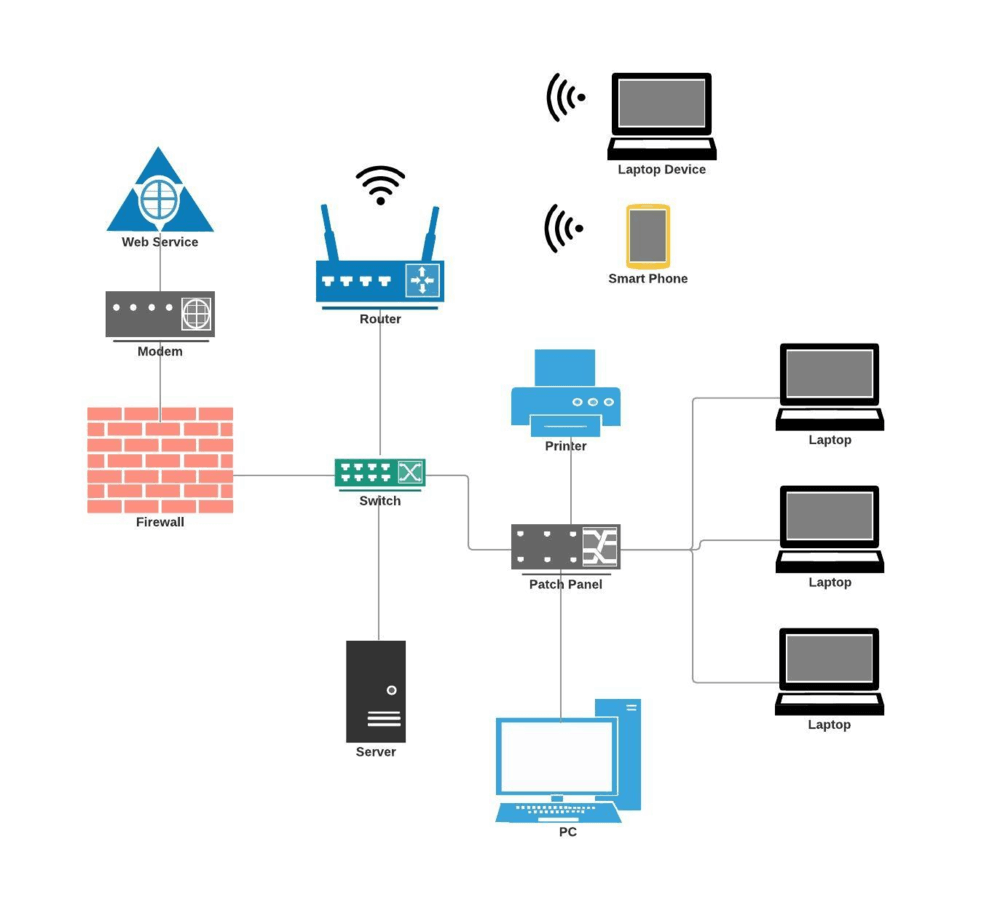
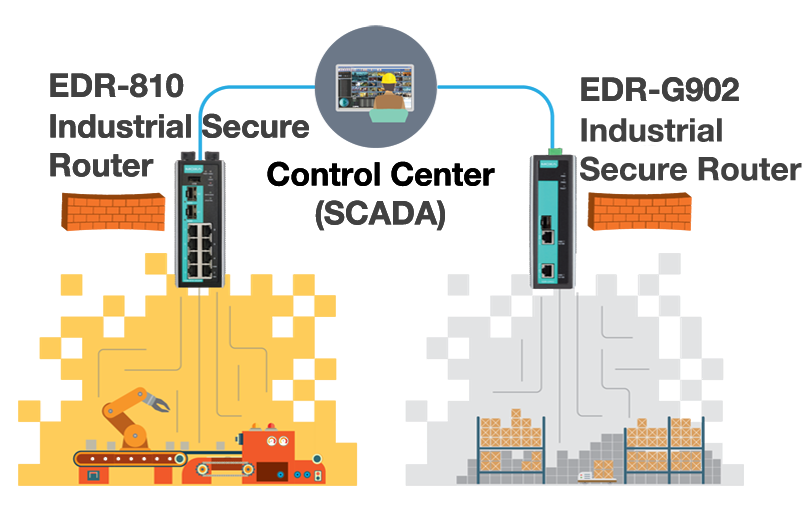
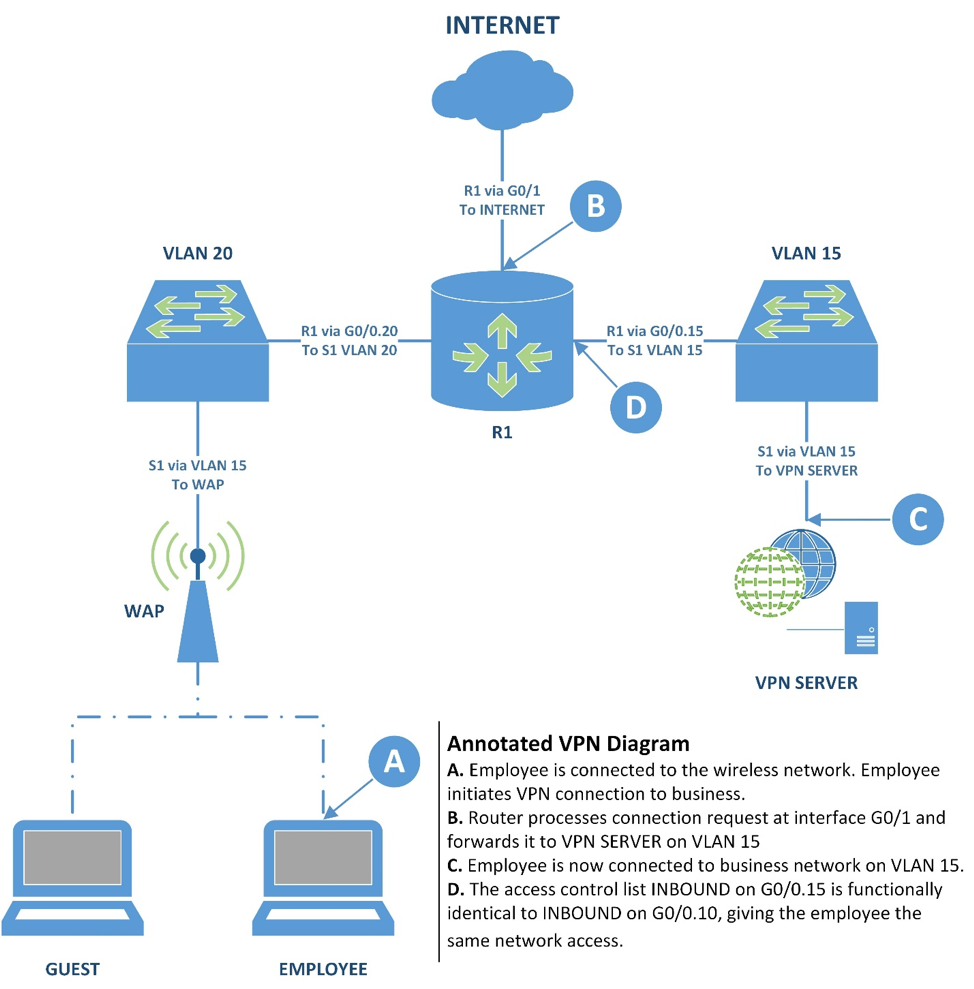
Fine Beautiful Info About How To Build A Secure Network
3.9k views 1 year ago.
How to build a secure network. October 29, 2021 leave a comment. Unplug your modem (and router, if you have one) for a few seconds. Create a secure wireless network.
Doing so will force your modem through a power cycle and might fix some dns issues. Dec 04, 2017 6 mins. Securing your home network involves different types of changes, some on your router, some on the devices attached to your home network, and some in your.
Mac address restriction. You can use them individually or in combination to build stronger defenses against network compromise. By vlad pivtorak | january 11, 2024.
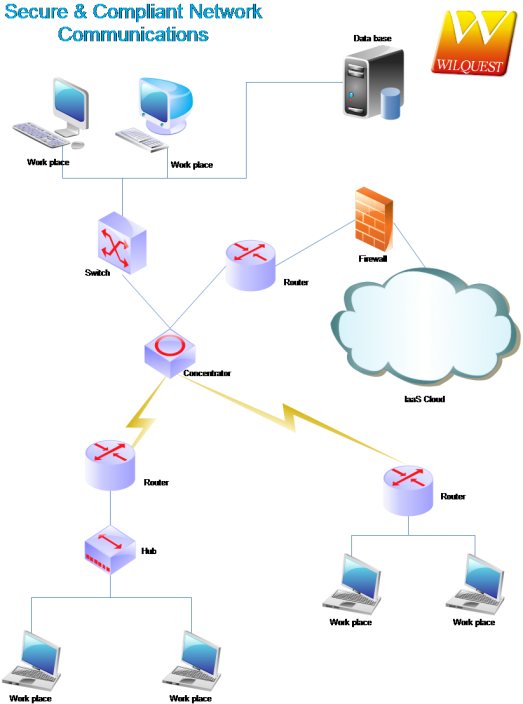
Employ multiple complementary approaches to security enforcement at various points in the network, therefore removing single points. The first step to build a secure network is to capture a complete picture of the it environment including all internal and external assets and vendor relationships. We will also discuss various strategies, tools, and best practices to build secure network infrastructure.
By mahendra ramsinghani. Build a wireless network that is secure from a variety of attack vectors. In this video we’ll talk about a few ways you can set up a secure.
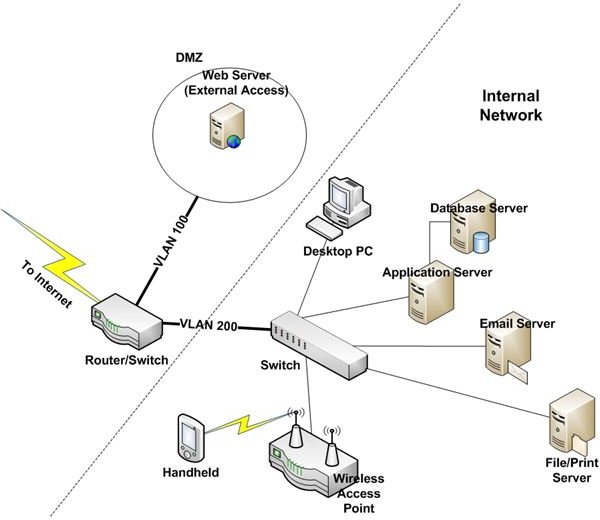
What is network security for businesses? Seamless connectivity is a valuable asset for your business, but it also comes with inherent risks. A firewall acts as a barrier between your network and the outside world, as it monitors incoming and outgoing network traffic.
Learn what the main differences are and how to establish cloud. How to build a strong secure network. How to build a fast and secure network.
Building a secure network in the cloud is different from securing a traditional network. Before embarking on the journey to a secure home network, it’s essential to understand your existing setup. Be an ms/tp network and bacnet ms/tp devices to send requests and responses among a defined group of devices.
Here’s what else to consider.